WCF Message Level Security by Example
This article will describe how to implement WCF message level security. It will show you the required steps to create the WCF library, host it in IIS, secure with Message Level Security, client application and finally see encrypted messages using WCFTraceViewer.
WCF Security
WCF provides three modes of security. Transport, Message, and TransportWithMessageCredential. Transport security can be achieved with SSL over HTTP(HTTPs). This article elaborates on Message Level security. TransportWithMessageCredential is a combination of the other two.
What is WCF Message Security
Message level security encrypts request and response messages using WS-Security specifications. It encloses security credentials and claims with every message. Each message either signed or encrypted. Message Security provides end-to-end channel security and is independent of the transport protocol. In short mutual authentication and message security is delivered at the message level.
Advantages of Message Level security in WCF
- Message Security provides multiple levels of security meaning that different parts (header, body, etc) of the message can be secured by different encryption methods.
- Message Security is not dependent on WCF protocols. It provides security regardless of binding used.
- Message Security provides end-to-end security, in Transport Security where once the message received at the server it is not encrypted whereas in Message Level security it is still encrypted.
- Message security is the only option to provide security when you have intermediate routers to route request and response.
Implementation of Message Level Security in WCF
Creation of WCF Service Library
Go through Create a WCF Service and Test using WCFTestClient. It creates basic WCF Service which has OperationContracts to return Product details from Products.xml.
Host ProductService in IIS
For this article, we will use HTTP protocols and host service in IIS. Unlike Transport Security you do not need to make any changes in IIS for Message Level Security.
Configure WCF Message Level Security
Open the NorthwindServices service library which you created in the first step and open its App.config file.
Here we will configure bindingConfiguration element of endpoint. Add <bindings> section under <system.serviceModel>
Set security mode as Message and clientCredentialType as Windows.
Your <system.serviceModel> configuration should look like
<system.serviceModel>
<services>
<service name="NorthwindServices.ProductService"
behaviorConfiguration="ServiceBehavior">
<host>
<baseAddresses>
<add baseAddress =
"http://localhost:7741/NorthwindServices
/ProductService/" />
</baseAddresses>
</host>
<endpoint address ="" binding="wsHttpBinding"
contract="NorthwindServices.IProducts"
bindingConfiguration ="wsMessage">
<identity>
<dns value="localhost"/>
</identity>
</endpoint>
<endpoint address="mex" binding="mexHttpBinding"
contract="IMetadataExchange"/>
</service>
</services>
<behaviors>
<serviceBehaviors>
<behavior name="ServiceBehavior" >
<serviceMetadata httpGetEnabled="true" />
</behavior>
</serviceBehaviors>
</behaviors>
<bindings>
<wsHttpBinding>
<binding name ="wsMessage">
<security mode ="Message">
<message clientCredentialType ="Windows"/>
</security>
</binding>
</wsHttpBinding>
</bindings>
</system.serviceModel>
clientCredentialType
clientCredentialType can have any value from below available options for Message Level Security.
- None: Messages are secured with encryption however it does not perform any authentication.
- Windows: Messages are secured with encryption and clients are authenticated using built in Windows Authentication which can be through Active Directory or NTLM.
- UserName: Messages are secured and encrypted and clients are authenticated by provided UserName and Password.
- Certificate: Messages are encrypted and both service and clients are authenticated with certificates.
- IssuedToken: Messages are encrypted and authentication happens through issued tokens by an authority like Cardspace.
Client Application
Create a new console application as a client for this WCF service. Add service reference of ProductService to the client application.
Add below client code to console application.
using NorthwindApp.ProductServiceRef;
namespace NorthwindApp
{
class Program
{
static void Main(string[] args)
{
ProductsClient client = new ProductsClient();
string cateName = client.GetCategoryName(1);
Console.WriteLine(cateName);
Console.Read();
}
}
}
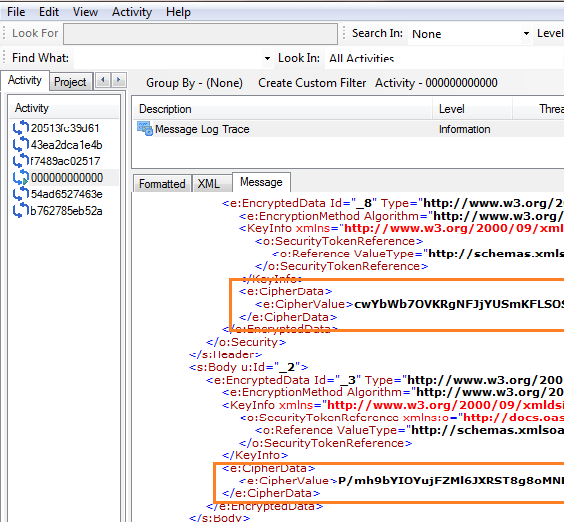
Enable WCF Tracing and Message Logging for a client application to see how the communication has encrypted. Execute application and open SvcTraceViewer. SvcTraceViewer is located at C:\Program Files (x86)\Microsoft SDKs\Windows\v7.0A\Bin.
Trace and Messages must have generated after execution of client application. Open it and notice how messages are encrypted.
Blog Search
-
Building Scalable Applications: Microservice Architecture Challenges
-
The Paradigm Shift to Low-Code and No-Code Development in Software Engineering
-
How To Use AutoMapper in ASP.NET Core Web API
-
Generate Log using Serilog And Seq In ASP.NET Core MVC 6
-
How to Setup CORS Policies in ASP.NET Core Web API


very good article that enlightening wcf message security
working on it.
The message could not be processed. This is most likely because the action 'http://tempuri.org/ICloudMitoService/GetCarrierList' is incorrect or because the message contains an invalid or expired security context token or because there is a mismatch between bindings. The security context token would be invalid if the service aborted the channel due to inactivity. To prevent the service from aborting idle sessions prematurely increase the Receive timeout on the service endpoint's binding.
@sachin, increase readerquota values for binding <basicHttpBinding> <binding name="LargeBuffer" ... <readerQuotas maxDepth="2147483647" maxStringContentLength="2147483647" maxArrayLength="2147483647" maxBytesPerRead="2147483647" maxNameTableCharCount="2147483647" /> .... </binding>
i am calling Restful services from iOS device . i want to implement secure communication over network between server(services hosted) and device. i want to prevent from unauthorized(via proxy server/burp's/ privileged escalation) interfere into request or response data. i tried with wsHttpBinding it is not encrypting data while calling from iOS device.